V2X-DAA
Direct Anonymous Attestation (DAA) as an alternative trust model for V2X security
- Project Name: V2X-DAA — DAA-enabled Security for Cooperative, Connected & Automated Mobility (CCAM)
- Duration: January 2021 – March 2022
- Funding: Bilateral industry collaboration (with UBITECH)
- Links: UBITECH announcement
- My Role: Project Initiator / Technical lead for architecture & evaluation
TL;DR
- Problem: PKI-based V2X scales poorly and strains privacy: bulk pseudonym provisioning, CRLs, and backend dependency. (Giannetsos & Krontiris, 2019)
- Idea: Move trust to the vehicle using Direct Anonymous Attestation (DAA) + TPM. Vehicles self-issue unlinkable pseudonyms; revocation is device-enforced (no CRLs). (Larsen et al., 2021)
- Evidence: We built both PKI and DAA pipelines on an ETSI-aligned V2X stack and measured them head-to-head. Under realistic channel loads, end-to-end latency converges, while DAA delivers cleaner revocation and no refill logistics. (Angelogianni et al., 2023)
Why PKI struggles at scale
Modern SCMS/CCMS deployments rely on central authorities to mint and refresh thousands of short-lived pseudonyms per vehicle and to distribute revocation state. This is operationally heavy, connectivity-sensitive, and creates privacy pressure even with separation-of-duties. (Giannetsos & Krontiris, 2019)
Our approach: vehicle-centric trust with DAA
We designed a V2X security architecture that anchors trust in the vehicle:
- On-board pseudonym self-issuance. A TPM creates and protects pseudonym keys; messages are signed with anonymous, unlinkable DAA signatures. (Larsen et al., 2021)
- Hardware-enforced policies. A revocation index inside the TPM binds each pseudonym to two states:
- Soft revocation: disable a specific pseudonym.
- Hard revocation: disable all pseudonyms of a vehicle in one shot. (Larsen et al., 2021)
- Privacy-preserving control plane. Vehicles register only cryptographic revocation hashes (“Proof of Registration”); no identity resolution is needed to revoke. (Larsen et al., 2021)
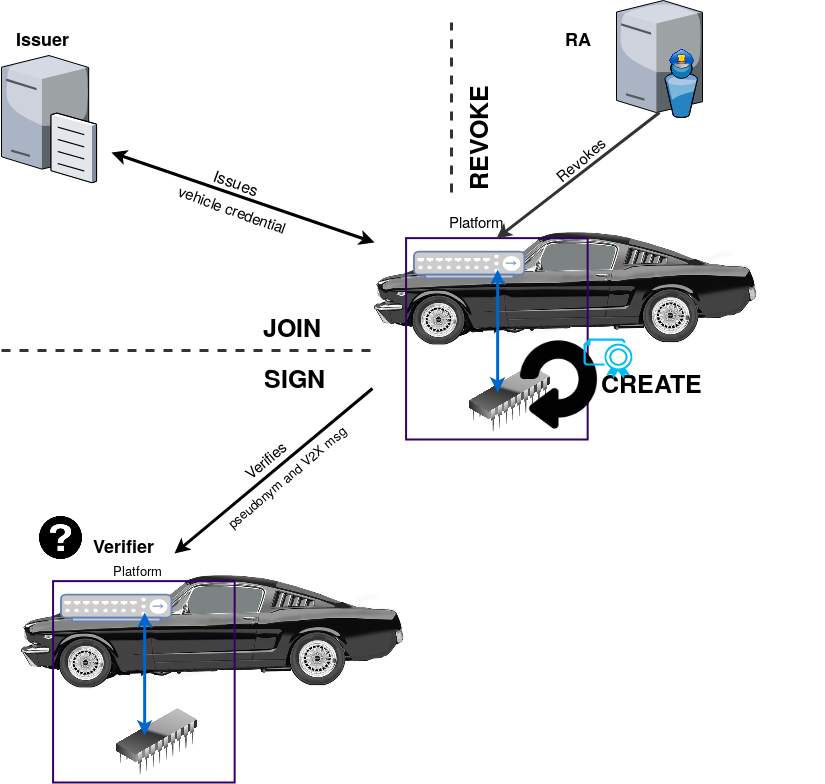
What we actually built
- A full DAA pipeline (JOIN → self-issuance → sign/verify → soft/hard revocation) on V2X-grade hardware, and a PKI baseline (OpenSSL/ECDSA), both integrated with an ETSI-aligned CAM/DENM stack for like-for-like measurement. (Angelogianni et al., 2023)
- A testbed exercising crypto cost, end-to-end latency under increasing message rates, pseudonym lifecycle, and revocation workflows. (Angelogianni et al., 2023)
Key results (what changed)
- Revocation becomes practical. One signed broadcast from the RA triggers local (TPM-enforced) revocation, either a single pseudonym or the entire set. No CRLs, no identity resolution. (Larsen et al., 2021)(Angelogianni et al., 2023)
- Self-issuance removes refill logistics. Pseudonyms are generated on-board under TPM policy; back-end load and connectivity assumptions drop dramatically. (Angelogianni et al., 2023)
- Latency remains viable. Although DAA signatures are heavier than ECDSA in isolation, under realistic channel loads the network/stack dominates, and DAA ≈ PKI in end-to-end latency, so DAA is practically deployable for safety messaging. (Angelogianni et al., 2023)
Why this matters
- Scalability: Eliminates bulk certificate manufacturing, distribution, and storage at fleet scale. (Giannetsos & Krontiris, 2019)
- Privacy by design: Unlinkable, on-device credentials minimize tracking risk while preserving verifiability. (Larsen et al., 2021)
- Operational security: A device kill-switch for misbehavior (hard revoke) with immediate effect, without revealing or resolving long-term identity. (Larsen et al., 2021)
References
- Securing V2X Communications for the Future: Can PKI Systems offer the answer?In Proceedings of the 14th International Conference on Availability, Reliability and Security (ARES ’19), Canterbury, CA, United Kingdom, Oct 2019
- Comparative Evaluation of PKI and DAA-based Architectures for V2X Communication SecurityIn 2023 IEEE Vehicular Networking Conference (VNC), Oct 2023